Introduction
Cyber Threats In our increasingly computerized world, digital threats have become a clear concern for people, organizations and states. And understanding these threats is critical to realizing information security.
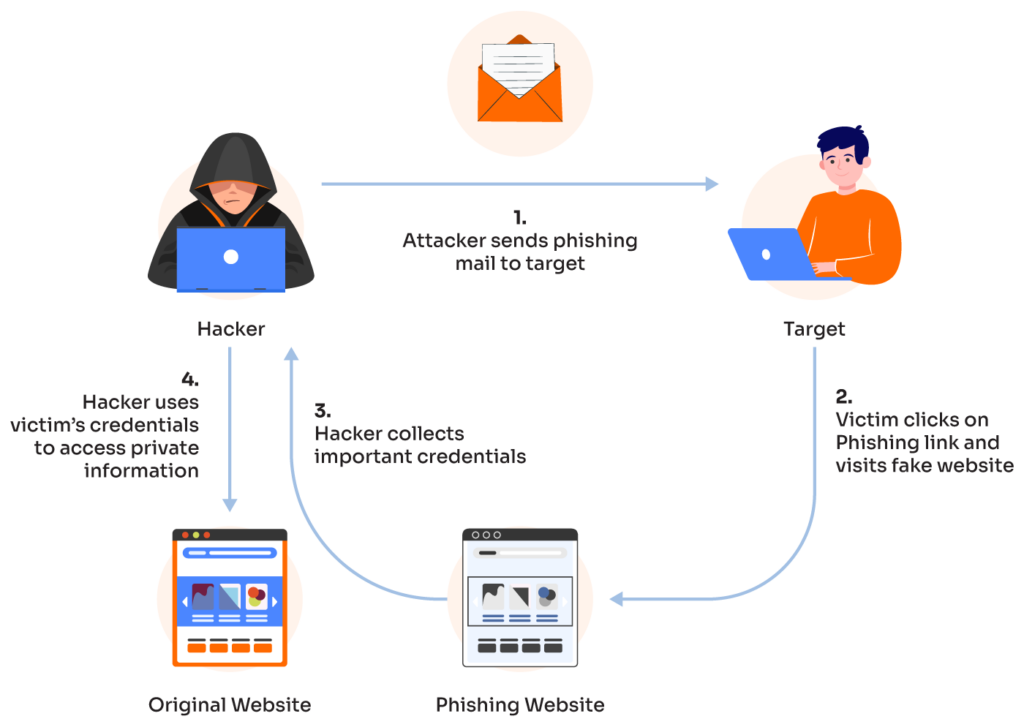
1. Cyber Threats Phishing Attacks
What is Phishing?
Phishing is a Cyber Threats that uses covered messages as a weapon. The objective is to fool the email beneficiary into enduring that the message is something they need or need — a deals from their bank, for instance, or a note from someone in their association — and to click an association or download an association.
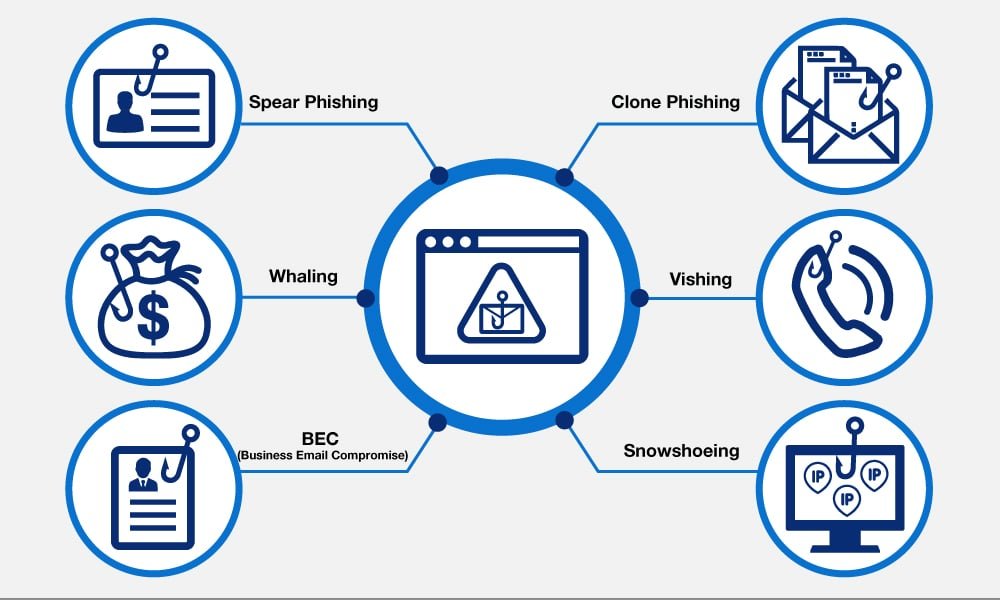
Types of Phishing Attacks
- Email Phishing: The most well-known type of phishing, where aggressors send mass messages to however many locations as could be allowed.
- Spear Phishing: A more designated approach where assailants tailor their messages to a particular individual or association.
- Whaling: Like lance phishing, however targets high-profile people like leaders.
- Smishing and Vishing: Phishing assaults led by means of SMS (smishing) or voice calls (vishing).
Impact of Phishing
Phishing can lead to significant financial loss, unauthorized access to sensitive data, and reputational damage. Successful phishing attacks can compromise personal information, login credentials, and even install malware on the victim’s device.
Mitigation Strategies
- Education and Awareness: Regular training programs to educate employees about recognizing phishing attempts.
- Email Filters: Implementing advanced email filtering solutions to detect and block phishing emails.
- Multi-Factor Authentication (MFA): Adding an additional layer of safety to login processes.
- Incident Response Plan: Having an arrangement set up to answer rapidly to phishing assaults.
2. Cyber Threats Malware
What is Malware?
Malware, short for vindictive programming, is any product deliberately intended to make harm a PC, server, client, or PC organization. It can take the form of viruses, worms, Trojan horses, ransomware, spyware, adware, and more.
Types of Malware
- Viruses: Pernicious programming joined to one more program that can duplicate and spread to different frameworks.
- Worms: Independent programming that recreates itself to spread to different PCs.
- Trojan Horses: Noxious programming masked as real programming.
- Ransomware: Software that encrypts the victim’s data and demands a ransom for the decryption key.
- Spyware: Programming that covertly screens and gathers data about clients.
- Adware: Programming that normally shows or downloads publicizing material.
Impact of Malware
The impact of malware can range from annoying advertisements and slowed system performance to severe data breaches, financial loss, and system outages. Ransomware attacks, in particular, can cripple organizations by locking them out of critical data and systems.
Mitigation Strategies
- Antivirus and Anti-Malware Software: Regularly updated security software to detect and remove malware.
- Firewalls: Carrying out strong firewalls to hinder unapproved access.
- Regular Updates and Patching: Staying up with the latest to close weaknesses.
- Backup and Recovery Plans: Guaranteeing customary reinforcements are made and tried for recuperation if there should be an occurrence of an assault.
3. Cyber Threats Ransomware
What is Ransomware?
Ransomware is a kind of malware that encodes the loss’ records. The aggressor then, at that point, requests a payoff from the casualty to reestablish admittance to the information upon installment. Ransomware assaults can target people, organizations, and, surprisingly, basic foundation.
Types of Ransomware
- Crypto Ransomware: Encodes documents and requests installment for the unscrambling key.
- Locker Ransomware: Locks the victim out of their device, preventing access to any files or applications.
- Scareware: Pretends to be a legitimate program but scares the user into paying a ransom to fix non-existent issues.
Impact of Ransomware
The impact of ransomware can be devastating, leading to significant financial loss, data loss, and operational disruption. Paying the result doesn’t guarantee data recovery and can empower further attacks.
Mitigation Strategies
- Regular Backups: Keeping up with cutting-edge reinforcements of every basic datum.
- Security Software: Using comprehensive security software to detect and prevent ransomware.
- User Training: Instructing clients about the risks of ransomware and safe figuring rehearses.
- Incident Response: Having a reasonable arrangement for answering ransomware assaults, including lawful and advertising viewpoints.
4. Cyber Threats Social Engineering
What is Social Engineering?
Social planning is a control system that exploits human slip-up to obtain private information, access, or assets. It relies on human psychology rather than technical hacking techniques to trick individuals into breaking normal security procedures.
Cyber Threats Types of Social Engineering Attacks
- Pretexting: Making what is happening to take a loss’ own personal information.
- Baiting: Offering something enticing to lure victims into revealing information or performing an action.
- Quid Pro Quo: Offering a help or advantage in return for data.
- Tailgating: Following somebody into a confined region without legitimate verification.
Cyber Threats Impact of Social Engineering
Successful social engineering attacks can lead to unauthorized access to sensitive information, financial loss, and compromised systems. They are often the first step in larger attacks, such as malware infections or data breaches.
Mitigation Strategies
- Security Awareness Training: Regular training to help employees recognize and respond to social engineering tactics.
- Verification Processes: Implementing procedures to verify identities before sharing information or granting access.
- Access Controls: Restricting access to sensitive areas and information to authorized personnel only.
- Incident Reporting: Encouraging employees to report suspicious activities immediately.

5. Refusal of Administration (DoS) and Circulated Forswearing of Administration (DDoS) Assaults
What are DoS and DDoS Attacks?
A Denial of Service (DoS) attack aims to make a machine or network resource unavailable to its intended users by overwhelming it with a flood of illegitimate requests. A Distributed Denial of Service (DDoS) attack is similar but involves multiple compromised Cyber Threats a single target, making it more challenging to defend against.
Types of DoS and DDoS Attacks
- Volume-Based Assaults: Overpower the transmission capacity of the objective.
- Protocol Attacks: Exploit weaknesses in the protocol stacks to exhaust server resources.
- Application Layer Attacks: Target the application layer to crash the web server.
Impact of DoS and DDoS Attacks
These Cyber Threats can cause significant downtime, loss of revenue, and reputational damage. They can also serve as a smokescreen for other malicious activities, such as data breaches.
Mitigation Strategies
- DDoS Protection Services: Using services specifically designed to detect and mitigate DDoS attacks.
- Network Monitoring: Continuous monitoring of network traffic to detect and respond to abnormal patterns.
- Rate Limiting: Implementing rate limiting to control the number of requests a server can handle.
- Redundancy and Failover: Having redundant systems and failover mechanisms to maintain service availability.
6. Man-in-the-Middle (MitM) Attacks
What is a Man-in-the-Middle Attack?
A Man-in-the-Center (MitM) assault happens when an aggressor covertly blocks and transfers messages between two gatherings who accept they are discussing straightforwardly with one another. This allows the attacker to steal information, inject malicious content, or impersonate one of the parties.
Types of MitM Attacks
- Packet Sniffing: Capturing data packets as they travel across a network.
- Session Hijacking: Taking control of a user’s session after they have logged in.
- SSL Stripping: Downgrading a secure HTTPS connection to an insecure HTTP connection.
- Wi-Fi Eavesdropping: Intercepting data transmitted over an unsecured Wi-Fi network.
Impact of MitM Attacks
MitM assaults can prompt the burglary of delicate data, for example, login qualifications, monetary information, and individual data. They can also result in the distribution of malware and unauthorized access to systems.
Mitigation Strategies
- Encryption: Using strong encryption protocols (e.g., HTTPS, TLS) to protect data in transit.
- VPNs: Employing Virtual Private Networks to create secure communication channels.
- Secure Wi-Fi: Ensuring Wi-Fi networks are secured with strong passwords and encryption.
- Two-Factor Authentication: Adding an extra layer of security to user authentication processes.
7. Cyber Threats Insider Threats
What is an Insider Threat?
An insider threat originates from within the organization, typically from employees, former employees, contractors, or business associates who have inside information concerning the organization’s security practices, data, and computer systems Cyber Threats.
Types of Insider Threats
- Malicious Insiders: Individuals who intentionally harm the organization for personal gain or revenge.
- Negligent Insiders: Employees who inadvertently cause harm through careless actions.
- Compromised Insiders: Representatives whose records or qualifications have been undermined by outer assailants.
Impact of Insider Threats
Insider dangers can prompt information breaks, monetary misfortune, and harm to an association’s standing. They are particularly challenging to detect and prevent because insiders typically have legitimate access to systems and data.
Mitigation Strategies
- Access Controls: Restricting admittance to delicate information and frameworks to just the individuals who need it.
- Monitoring and Auditing: Continuously monitoring user activity and conducting regular audits.
- Behavioral Analysis: Using advanced analytics to detect unusual behavior that may indicate an insider threat.
- Security Policies: Implementing and enforcing comprehensive security policies and procedures.
8. Cyber Threats Advanced Persistent Threats (APTs)
What are Advanced Persistent Threats?
Advanced Persistent Threats (APTs) are prolonged and targeted Cyber Threats in which an intruder gains access to a network and remains undetected for an extended period. APTs mean to take information instead of cause prompt harm.
Stages of APT Attacks
- Initial Intrusion: Gaining access to the network through spear phishing, exploiting vulnerabilities, or other methods.
- Establishing a Foothold: Installing malware to maintain access.
- Escalating Privileges: Gaining higher levels of access within the network.
- Internal Reconnaissance: Exploring the network to identify valuable data and assets.
- Data Exfiltration: Stealing data and transferring it out of the network.
- Maintaining Presence: Ensuring continued access for future operations.
Impact of APTs
APTs can result in the theft of sensitive information, intellectual property, and strategic data. They pose a significant threat to national security, critical infrastructure, and large enterprises.
Mitigation Strategies
- Threat Intelligence: Using threat intelligence to identify and respond to APT indicators.
- Network Segmentation: Dividing the network into segments to limit the movement of attackers.
- Intrusion Detection Systems (IDS): Deploying IDS to detect unauthorized activities.
- Regular Security Assessments: Conducting regular security assessments and penetration testing to identify vulnerabilities.
Conclusion
Cyber Threats are evolving rapidly, and understanding the various types and their potential impact is crucial for developing effective security measures. By staying informed about common Cyber Threats and implementing robust security practices, individuals and organizations can better protect themselves against these ever-present dangers. Regular training, advanced security technologies, and a proactive approach to threat detection and response are essential components of a comprehensive Cyber Threats strategy.

